At the 2017 Ovation Users Group conference, Emerson’s Steve Schilling discussed the rapid changes going on in the power, water and wastewater industries and the changes in technology required to keep up with these changes.
At the 2017 Ovation Users Group conference, Emerson’s Steve Schilling discussed the rapid changes going on in the power, water and wastewater industries and the changes in technology required to keep up with these changes.
Steve opened highlighting some of the key issues worrying people in these industries—reliability, reliable integration of renewables and distributed energy resources (DER), security, aging infrastructure, aging workforce and business models/regulatory reform.
To address these areas of high concern, Steve discussed some of the ways technology has been developed to help. Scalability is an important area to be able to handle applications from DERs and microgrids to large scale facilities.
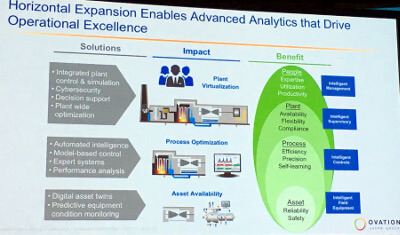 The key to the technology strategy for Ovation to be a single platform for an infinite number of solutions—utility scale renewables, remote monitoring and diagnostics, DCS cybersecurity, data analytics, boiler control, turbine control, safety instrumented systems, machinery health, excitation control, simulator/virtual plants, transmission and distribution and DERs.
The key to the technology strategy for Ovation to be a single platform for an infinite number of solutions—utility scale renewables, remote monitoring and diagnostics, DCS cybersecurity, data analytics, boiler control, turbine control, safety instrumented systems, machinery health, excitation control, simulator/virtual plants, transmission and distribution and DERs.
Feature packs add functionality and are applied like patches without requiring major upgrades. Steve described new and upcoming hardware functionality in Ethernet I/O, remote I/O and hardware-based data encryption.
From a software standpoint, the coming Ovation Object Builder provides a platform for scalable applications. It makes applications more repeatable by replicating proven control strategies across similar equipment.
From a cybersecurity standpoint, some additions coming include secure boot at the chip level, file signing and data encryption. In an earlier post, Comprehensive Cybersecurity for Critical Infrastructure, we highlighted some of the applications and programs that also help improve ongoing security efforts.
From a simulation standpoint, Steve described the use of Cloud services to host the virtual plant models and use additional deep analytics to find ways to improve efficiency and reliability.
Related Posts
The post Technology Advancements for Power, Water & Wastewater Industries appeared first on the Emerson Automation Experts blog.










 There are many paths to pursue in improving cyber defenses for industrial control systems (ICS). At the 2017 Ovation Users Group conference, Emerson’s Tom Kizer presented on applying threat intelligence for system defense.
There are many paths to pursue in improving cyber defenses for industrial control systems (ICS). At the 2017 Ovation Users Group conference, Emerson’s Tom Kizer presented on applying threat intelligence for system defense.





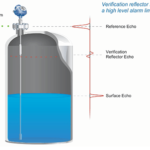
 communication that can use frequency monitoring to know if the switch is in oil, water or alcohol. They can detect settled sediment within a liquid and can even detect the presence of foam.
communication that can use frequency monitoring to know if the switch is in oil, water or alcohol. They can detect settled sediment within a liquid and can even detect the presence of foam.